Why Fiber Network Security Is Critical for Protecting Sensitive Data and Communications
Comprehending the Significance of Information and Network Safety in Today's Digital Age
In an age where digital makeover is essential to service success, the significance of information and network protection has actually never been much more noticable. Comprehending the repercussions of data breaches, together with the essential security procedures required to alleviate these risks, ends up being essential.
The Increase of Cyber Dangers
The landscape of digital safety has actually come to be significantly perilous as cyber risks proliferate worldwide. Organizations throughout numerous fields are facing a rise in innovative strikes, varying from ransomware to phishing schemes. These threats not just endanger delicate information yet additionally interfere with service procedures, bring about substantial economic losses and reputational damage.

Moreover, the development of advanced techniques such as expert system and equipment learning has actually geared up enemies with the tools to automate their operations, making it significantly challenging for standard protection measures to maintain rate. As services browse this treacherous landscape, the necessity for durable data and network protection strategies has actually never ever been higher, highlighting the demand for cautious tracking, timely updates, and employee awareness to mitigate these escalating threats.
Effects of Information Breaches
Data violations can have far-ranging and severe implications for companies, affecting not only their financial standing however additionally their credibility and consumer depend on. When sensitive info is jeopardized, organizations usually deal with direct economic losses as a result of legal fees, governing fines, and the prices associated with case response. Additionally, the lasting results can be much more harmful; a damaged track record may cause lost organization chances and decreasing consumer retention.
The erosion of client trust fund is maybe the most dangerous consequence of an information violation. Clients might wonder about an organization's ability to shield their individual info and, because of this, might select to take their business elsewhere. This loss of self-confidence can cause lowered income and market share.
Furthermore, organizations may experience enhanced examination from stakeholders and regulatory authorities, resulting in a much more difficult functional atmosphere. The psychological influence on employees, who may feel less protected or valued, can also affect efficiency and spirits.
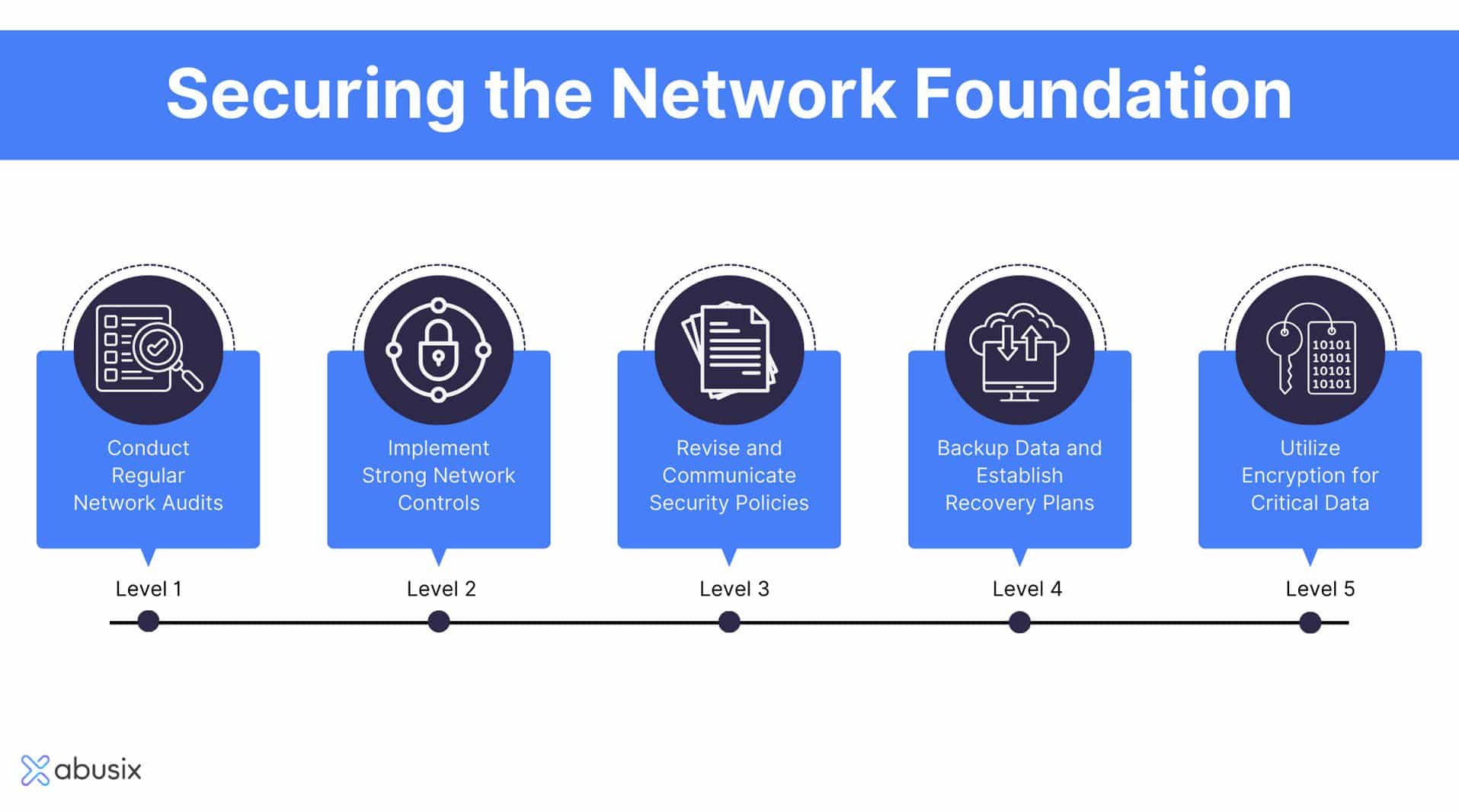
Important Protection Measures
Carrying out essential protection actions is crucial for guarding sensitive details and keeping business honesty. Organizations has to take on a multi-layered protection technique that encompasses both electronic and physical safeguards.
One of the fundamental actions is to establish robust accessibility controls, guaranteeing that only authorized employees can access delicate information. This can be achieved via solid password plans, multi-factor authentication, and regular audits of individual access legal rights. Additionally, securing information both en route and at rest supplies an essential layer of security against unapproved gain access to.
Routine software application updates and spot administration are additionally crucial, as they aid reduce vulnerabilities that might be manipulated by destructive stars. Organizations must execute firewall softwares and intrusion discovery systems to keep track of network traffic and identify prospective threats proactively.
Furthermore, carrying out normal protection evaluations and infiltration screening enables organizations to recognize weak points in their defenses prior to they can be made use of. Worker training on security recognition is similarly essential, as human mistake stays one of the leading sources of data violations. By incorporating these necessary safety and security measures, companies can significantly lower their threat direct exposure and enhance their strength versus cyber hazards.
Structure a Safety Society
Developing an effective protection culture within an organization is a vital complement to carrying out durable protection steps. A safety and security culture promotes an environment where workers comprehend the importance of shielding delicate details and are actively involved in securing it. This culture is cultivated with detailed training programs that highlight the value of information safety and the possible risks linked with neglect.
Leadership plays a critical duty in establishing this culture. When executives focus on safety and demonstrate their dedication, employees are most likely to embrace similar attitudes (data and network security). Routine communication concerning protection policies, treatments, and updates makes certain that everybody stays informed and watchful
Motivating open dialogue concerning security worries empowers workers to report suspicious tasks without anxiety of revenge. Carrying out a rewards system for proactive behavior can fft pipeline protection additionally incentivize individuals to take possession of security methods.
Furthermore, performing drills and simulations aids enhance the value of readiness and reaction. By incorporating protection into day-to-day procedures and decision-making processes, companies can create a resilient workforce efficient in adapting to developing dangers. Eventually, a strong safety and security culture not only protects data but also boosts overall business stability and trustworthiness.
Future Trends in Information Security
Advancing and emerging technologies cyber threats are reshaping the landscape of data safety, prompting organizations to adapt their techniques accordingly. One substantial pattern is the raised fostering of artificial intelligence (AI) and device understanding (ML) for risk discovery and response. These modern technologies allow more proactive protection actions by analyzing substantial amounts of information to recognize anomalies and prospective breaches in real-time.
One more fad is the relocation in the direction of zero-trust safety and security models, which operate under the concept that no individual or gadget should be trusted by default. This technique emphasizes continual confirmation and lessens access to sensitive information based on stringent authentication procedures.
Furthermore, the surge of remote work has increased the demand for durable endpoint safety options that safeguard tools outside conventional network borders - data and network security. As companies embrace cloud computer, safeguarding data in transportation and at rest has become paramount, causing the growth of innovative security techniques
Final Thought
In final thought, the value of information and network security can not be overstated in the modern digital landscape. As cyber dangers remain to intensify, organizations have to remain aggressive and attentive in implementing comprehensive protection actions. The prospective effects of data violations underscore the necessity of securing sensitive information. Growing a culture of safety and security recognition and adjusting to arising trends will enhance strength versus evolving cyber threats, ultimately guaranteeing the security of beneficial properties and keeping stakeholder trust fund.
In an age where electronic makeover is important to service success, the importance of data and network protection has actually never been more obvious. Comprehending the repercussions of information breaches, alongside the crucial safety steps needed to alleviate these risks, comes to be vital.Creating a reliable safety and security culture within a company is an important enhance to executing durable security actions.Emerging modern technologies and progressing cyber threats are improving the landscape of information safety and security, motivating companies to adjust their approaches appropriately.In verdict, the significance of data and network security can not be overstated in the modern digital landscape.